Are you worried about the security of your API? Learn the best practices you need to implement to counter the security threat to your API today.
The evolving digital ecosystem has seen businesses scale their operations online, significantly transforming their business models and revenue generation. This has seen the rapid implementation of Application Programming Interfaces (APIs) by organizations that rely on them to deliver products and services to their customers.
However, with the upsurge of APIs, comes the greater risk of security concerns. Businesses need to ensure that the deployment of their APIs cause no security threats. This may include data breaches given that APIs are loaded with corporate and customer data, which need to be kept safe. As opposed to web applications, APIs have several unique challenges around security. Investing in the right API security solutions serves a great deal in securing your APIs.
In this post, we will discuss some of the major challenges and the best practices around API security-
Recognize the Risk and Map Attack Possibilities:
Most organizations and businesses using APIs to scale their businesses face the potential threat of exposing their corporate data. It is best practice to know your vulnerabilities and map in attack possibilities. Most developers are mainly focused on making features as robust as possible while paying very little interest to potential flaws within the API. Hackers then easily find a gateway to exploit the API.
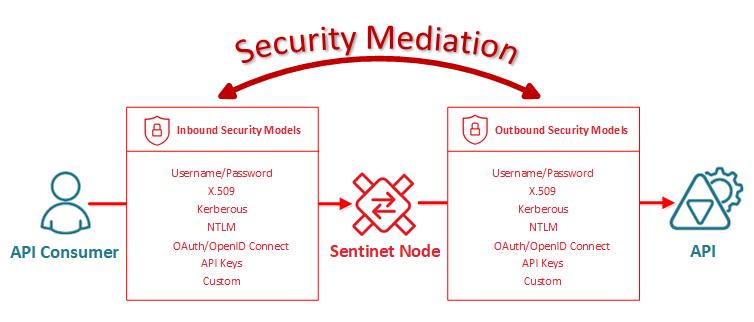
Implement Rigorous Authentication and Authorization Measures:
Any secure API provides authentication on both ends. Authentication provides reliable information about the end-user while authorization determines what resources the identified user has access to. Most enterprises have resorted to modern authentication methods, including biometric solutions like fingerprints. Another way organizations are protecting data is through encryption across the whole lifecycle of an API.
Monitor Add-On Software:
One of the common uses of interfaces is the use of third parties who write add-on apps in a platform. Commonly used on social media sites like Facebook, this provision allows developers high-level authorization rights, which hackers can easily get a chance to exploit.
Input Validation:
This is a step that allows the application to validate the user inputs within the defined parameters. This process is key to providing API security by filtering out malicious attacks and tracking dubious cases. This is one of the best-proven methods of protecting a system against common security threats.
Check Data on The Back-End:
Data on the back-end is mostly overlooked as most organizations concentrate their efforts on securing the front-end. This gives hackers an access point to exploit the system. It is vital to test security. Security testing is a task that requires time and resources. This should not in any way be undermined as it can reveal areas of API system vulnerabilities.
Invest in API Security and Tools:
With the advancement of technology, businesses need to invest and research on new tools that developers are using to manage APIs. These new security tools are available from established vendors to new startups offering vulnerability detection from runtime management to design, development, and test time threats. Some of the features of these security tools include pre-built security scans that check code, flaws, and improper data handling.
API usage is not about to slow down with the rate at which technology is advancing. Businesses need to upscale their efforts in securing their systems by ensuring they keep abreast of the rising security threats to close in on them in time.
Also, Read: What is API Management & its working












No Comments